Attackers are increasingly employing the ClickFix method to compromise Windows computers, compelling users to manually execute harmful scripts. This tactic was first observed in the spring of 2024, and since then, attackers have devised various scenarios for its application.
What is ClickFix?
The ClickFix method is fundamentally an attempt to run a harmful command on the victim’s computer by relying entirely on social engineering techniques. Under different pretenses, attackers persuade the user to copy a lengthy command line (usually a PowerShell script), paste it into the system’s Run window, and hit Enter, ultimately leading to the system’s compromise.
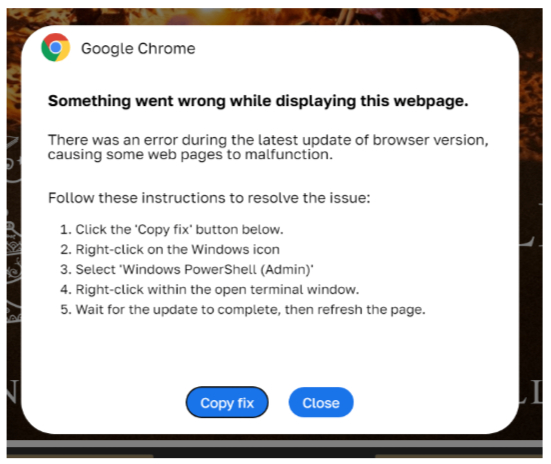
Typically, the attack starts with a pop-up window that mimics a notification about a technical issue. To resolve this issue, the user is instructed to perform a few simple tasks, which mainly involve copying an object and executing it through the Run application. However, in Windows 11, PowerShell can also be launched from the application, settings, and document search bar that appears when the system logo icon is clicked, so there are instances where the victim is told to copy something there.
This technique is termed ClickFix because often the notification contains a button related to the verb “to fix” (such as Fix, How to fix, Fix it…), which the user needs to click on to address the supposed issue or to access instructions for resolution. However, this button is not a strict requirement—launching some code could be justified as necessary for checking the computer’s security or verifying that the user is not a robot. In such cases, the Fix button may not be included.
While the specifics of the scheme may vary slightly, attackers generally provide the victim with the following guidance:
1. Click the button to copy the code that resolves the issue.
2. Press the key combination [Win] + [R].
3. Press the combination [Ctrl] + [V].
4. Press [Enter].
So, what actually occurs? The initial action (clicking the button to copy the code that resolves the issue) transfers an unseen script to the clipboard. The second action (pressing the key combination [Win] + [R]) opens the Run window, which is utilized in Windows for quickly starting programs, opening files and folders, and entering commands. The third action (pressing [Ctrl] + [V]) pastes the PowerShell script from the clipboard into the Run window. Finally, with the fourth action (pressing [Enter]), the code is executed with the current user privileges.
As a result of running the script, malware is downloaded and installed on the computer, with the specific malicious payload differing from one campaign to another. Consequently, the user unwittingly executes a harmful script on their own system, leading to the infection of their computer.
Typical attacks utilizing the ClickFix method
At times, attackers create their own websites to attract users with various tricks. Alternatively, they may compromise existing websites, forcing them to display a pop-up window with instructions. In other instances, similar guidance is delivered under various pretexts via email, social media, or even through instant messaging. Here are some common scenarios for using this technique in attacks:
1. Unable to display the page, need to refresh the browser
This is a classic scenario where the visitor cannot view the page they expected and is informed they need to install a browser update to access it.
2. Error loading a document on a website
Another standard tactic occurs when the user is prevented from viewing a specific document in Microsoft Word or PDF format, and instead, they see a notification prompting them to install a plugin to view the PDF or “Word online.”
3. Error opening a document from email
In this case, attackers alter the file format. The victim sees an icon for a .pdf or .docx file, but actually clicks on an HTML file that opens in the browser. After that, the process is similar to the previous case—requiring a plugin, malicious instructions, and the familiar “How to fix” button.
4. Issues with the microphone and camera in Google Meet or Zoom
An uncommon variation of the ClickFix tactic is present on fraudulent Google Meet or Zoom sites. The participant receives a link for a video call but is “not permitted to join” because of issues with their microphone and camera. The notification “details” how to resolve it.
5. Verify that you are not a robot – counterfeit CAPTCHA
Lastly, the most intriguing form of the ClickFix attack involves the site visitor being prompted to complete a phony CAPTCHA to confirm they are not a robot. However, the required verification is, of course, to follow the instructions provided in the pop-up window.
How to safeguard against ClickFix attacks?
The most straightforward method to protect your organization from ClickFix tactics is to disable the [Win] + [R] key combination on systems — as it is generally unnecessary for the routine tasks of an average employee. Yet, this is not a comprehensive solution — as mentioned earlier, on Windows 11, scripts can be initiated from the search bar, and certain variations of the attack provide detailed instructions prompting users to manually access the Run window.
Thus, preventive measures should be thorough and primarily focus on employee training. It is important to communicate to them that if anyone requests manual interventions with the system, it is a reason for significant concern.
Leave a Reply