-
Read More: Security in Android 15: What’s new?At the recent I/O 2024 developer conference held in California, Google unveiled the second beta…
-
Read More: Fraudsters are using AI-generated digital clones to bypass Know Your Customer (KYC) procedures and open money laundering accountsWhile humanity is attempting to recover the hundreds of billions of dollars invested in generative…
-
Read More: What to do if your mouse is double-clicking when you don’t mean itIs your mouse unexpectedly detecting two clicks even when you believe you’re only clicking once?…
-
Read More: Netflix is discontinuing support for certain older Fire TV devices starting in JuneNetflix has expanded the availability of its streaming applications to a variety of devices over…
-
Read More: Why ESPN’s new streaming service will cost $30 per monthLast week, ESPN announced the subscription price for the standalone streaming service it plans to…
-
Read More: Businesses reaching the “acceptance stage”: given inevitable breaches — how to prepare for them?Attacks targeting corporate IT infrastructure—particularly through ransomware—and various other cyber incidents are increasingly recognized as…
-
Read More: Trojan embedded in fake Android smartphonesThe well-known checkout process at the supermarket: after everything has been scanned, the cashier offers…
-
Read More: A popular blogger’s Instagram account was hijacked using a SIM-swap attack“I’m giving away $125,000! Join the project through the link in my profile!” — a…
-
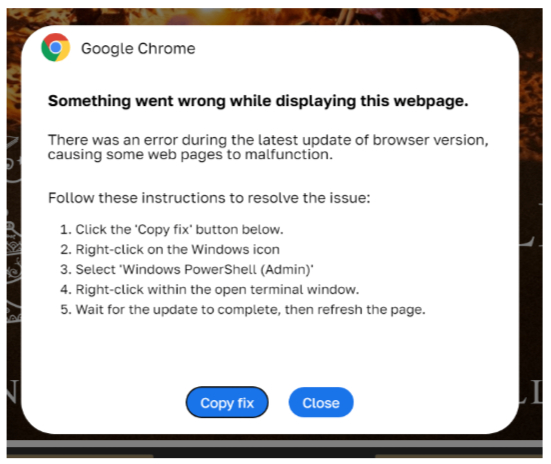
Read More: An infection tactic called ClickFix is becoming increasingly popular among cybercriminalsAttackers are increasingly employing the ClickFix method to compromise Windows computers, compelling users to manually…
-
Read More: Creating an unforgettable passwordThe influx of new information that we constantly face never slows down. By 2025, the…